Pegasus Spyware has emerged as a dangerous threat, as it requires one wrong click on a message or email to pass the entire phone to a remote bad guy. For example, the phone remains under hostile control forever. In some cases, applications such as Pegasus can be installed even if the user never clicks on the “trap” message. Given the ability of telephones to communicate their location, surveillance can only be set to start when the telephone enters certain target locations, such as secure government buildings, large corporations, entertainment studios, and more.
How can organizations and government agencies protect compromised mobile phones from Pegasus spyware? Log in to Bastille Networks.

Bastille Networks, recently a leader in detecting corporate threats through software-defined radio announced Bastille Enterprise gives corporations and agencies the ability to detect, detect, and mitigate radio transmitting threats from Pegasus Spyware. Pegasus Spyware demonstrates that a remote attacker can activate the camera and microphone of any mobile phone to filter out calls or video meetings. NSO Group, the Israeli manufacturer of Pegasus, claims that their system has never attacked a phone with an American phone number. However, the findings show that Pegasus used telephones on American soil that had foreign numbers.
 According to Chris Risley, CEO of Bastille Networks: NSO is not the only hacker team in the world that has these capabilities. Other spyware from other countries will not have the same hesitation to infect American phones. So everyone should increase their concern about the authorization of mobile phones in areas with confidential or classified information.
According to Chris Risley, CEO of Bastille Networks: NSO is not the only hacker team in the world that has these capabilities. Other spyware from other countries will not have the same hesitation to infect American phones. So everyone should increase their concern about the authorization of mobile phones in areas with confidential or classified information.
Bastille detects and locates unauthorized cell phones to create an accurate facility point plan, offering security situational awareness teams with features such as geozoning, hotspot detection, SIEMS integration, and forensics DVR. The following are examples of cases from businesses, defense and civilian agencies:
- Apply device policies: Detect cell phones in violation of cell phone policies for sensitive areas or areas without a cell phone.
- Scan tent sites, buildings and remote offices: Scan a room or building to find out the presence and location of all transmitters / transmitters and building systems.
- Secure Meeting Areas: Locate transmitting electronic devices in secure meeting areas.
“The Bastille has been researching and detecting RF and cell penetrations and research for the government for years, and the Pegasus Projects, which report this week, should put all businesses on the alert. Millions of vulnerable smartphones enter the workplace every day. A hacked smartphone can be used as a portal in the company’s network, putting at risk the sensitive and critical data of the organization to be violated. It is imperative to have security protocols to manage the safe use of smartphones in the workplace. “If security teams don’t think smartphones in the facility are an important threat in July, they should certainly think they’re an important threat now,” Risley added.
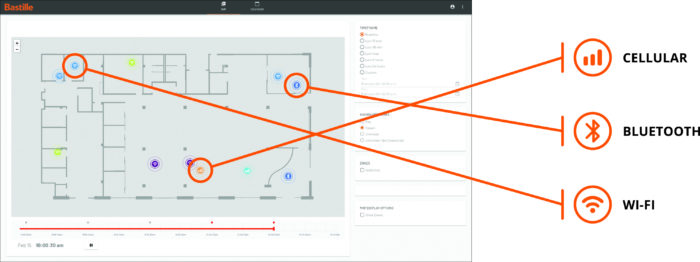
The US government is deeply concerned about Russia’s espionage, as national actors such as China, North Korea, Russia and Israel are very cunning in using RF techniques to disrupt network security. The government has accepted the threat of RF espionage, and therefore government facilities with valuable secrets have policies to turn off RF devices such as mobile phones to keep the threats at bay. While some government and commercial buildings have protected areas where mobile phones or other RF transmitting devices are not allowed, the detection and locating of radio devices is largely based on the honor or one-time device scanning system. Unfortunately, nation states and other bad actors do not follow the system of honor, and one-time scans are just that: one-time and cannot monitor 24 × 7.
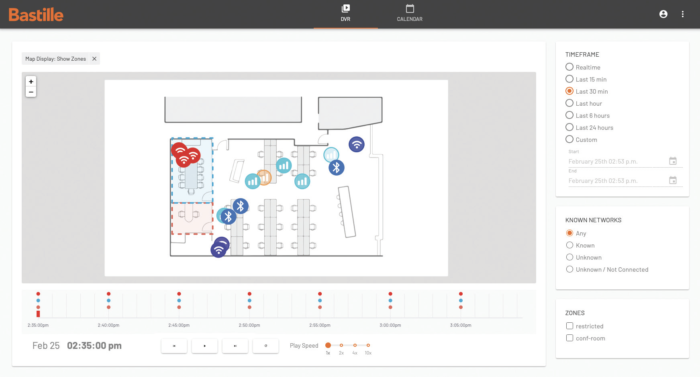
Bastille equips customers to find and locate all mobile phones in their facilities, whether these phones have Wi-Fi or Bluetooth. Remarkably, the Bastille is the only civilian product that can find cell phones indoors by detecting cellular signals. The Bastille ensures that there are no unauthorized mobile phones, therefore there are no infected phones in sensitive areas. Bastille is trusted by the military, government, and Fortune 500 customers to immediately detect, locate, and warn of fraudulent cell phones and other radio frequency (RF) -based devices throughout a facility.

